Windows Security Policy Wizard
The Windows Security Wizard guides the user in setting up the applications security policy and in assigning an administrator user. Using this security policy the user management will be linked to the windows host computer or the overall IT-infrastructure.
Windows Security Policy Wizard Step 1:
Select the button 'By Windows Security Policy'. The security policy selection dialog looks like this:
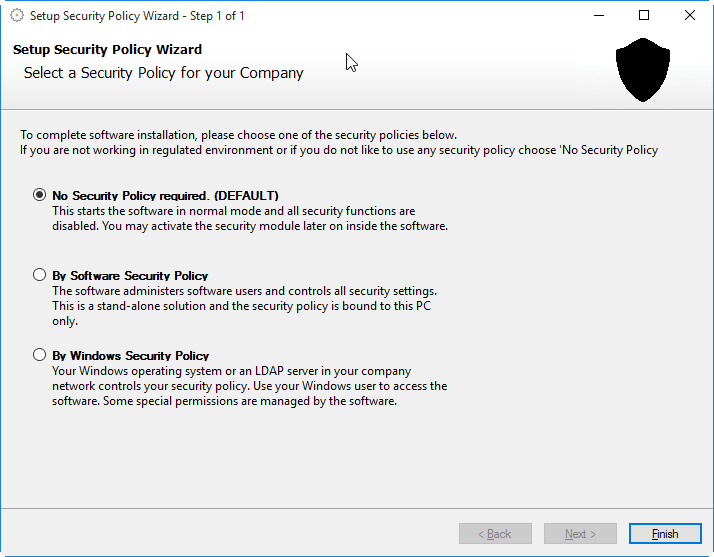
Windows Security Policy Wizard Step 2:
When selecting "By Windows Security Policy" radio button, the software will first try to find all LDAP-servers available:
All available servers will be listed in a dropdown box and the user then needs to select an appropriate server or the local windows computer from the list:
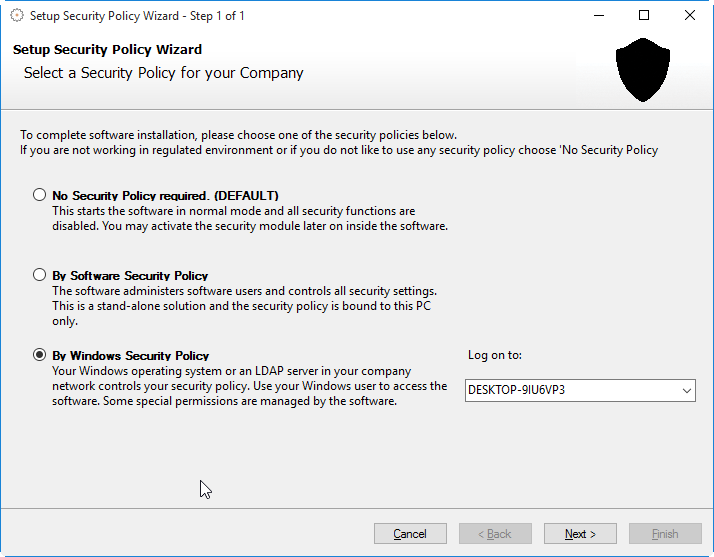
Windows Security Policy Wizard Step 3:
All users that have access to the selected server/computer will be retrieved:
The user that will be the administrator of the application needs to be selected from the dropdown box:
Windows Security Policy Wizard Step 4:
To complete the administrator selection the software needs to be restarted:
Software restart and first login
After restarting, the software will have finished the security policy setup and the user will be welcomed by the login screen. The user who has been chosen as administrator beforehand needs to log in using his windows user account password:
If there correct password has been entered, the software will prompt the administrator to continue with the Data Access Control setup:
The Data Access Control setup can be executed immediately or at a later point in time. In addition to the general security functions it will provide advanced user based data access control. If your working environment does not require data access control this setup can be skipped. Please review the chapter "Data Access Control" for further information.
Completing the security setup
After software security wizard has completed successfully, the basic security functions of the application are activated. The administrator will have access to the application with limited functionality. The security setup needs to be finalized by utilizing the following additional functions:
-
User Management - to add/authorize additional users
-
Permission Schemes - to configure access to software functions
Optionally additional security functions may be configured:
-
Data Access Control - to configure data access rules (if not already configured during the setup wizard)
-
Password Policy Options - to control password requirements
-
Activity logging - to record all application activity
-
Data versioning - to keep a version history of modified data
Please review the corresponding chapters for further information.